SSL secure browsing threats |
please flag with care:
| |
| 2007-12-19 | No history | 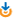 | Add My version | |
(mindmap file created by FreeMind)
| | |
| This is a mind map about Internet Security. From https://financialcryptography.com/ | |
 | |
| outline | |
SSL secure browsing threats
CA signed certs (CASC)
valid cert
under duress
"national security letter"
court action
extortion/blackmail
insider fraud
accident
acquire cert from CA
Level I - catch email auth
identity theft
failure of DD - has existing handle
re-issues v. issues fresh
another CA issues
failure of DD by CA
microsoft
CA loses key
root key
signing key
routine
revocation
not fast enough...
false revoke attack
not (widely) deployed
expiry
relying party ignores
expiries listed briefly in revocation
- cert failure
bug in cert layout
bug in cert protocol
root in browser
unknown root
not correct purpose
invalid root
root revoked
root falsely inserted
- browser failure
IE failed to check
disaster?
nobody noticed?
- client certs
rare
financial institutions prefer to accept 2-party authentication
merchants don't need identity, only token
relying on cert
steal the cert
can log other details
relying on name
get another issued
can cache and decline
Anon-DH
MITM
self-signed cert (SSC)
MITM on first access
MITM on uncached access
browser muffs fingerprint
down-grade attack
to weak cipher
to other known cert
to other cert with distinct role
Auth A to Auth B
practically, CASC -> HTTP
CASC -> SSC -> ADH -> HTTP
- Denial of Service
on user - force other means
on server
on router nodes
revocation?
bypass security
URL click-to-browse
site covers chrome
site ignores SSL
vast majority of phishing
bugs in browser
site uses SSL and cert
cert is correct - stolen?
click-thru-warnings
name is same - details not shown
name is close
name is apropos
random name
SSL with any name is often good enough
SSL
leaks information
KeyEx failure
exploit gap from Pk to Sk
ignores client cert
ignores server cert
protocol bug
break the crypto
break the protocol
bug in implementation
mixed attack
- HTTP on content, crypto on CC
eavesdrop content
travel
hotel
retail
CC covered by crypto
account registration
- eavesdropping attack
Identity theft
movements tracking
stalking
home schedule
extortion
public media
crack boxen
crack browser platform
eavesdrop on comms
insert dodgy root
change code
- crack server platform
eavesdrop
steal key
change code
replace key
bypass attack app directly
steal credit card database
steal user identity info
change code
initiate actions directly
crack (router) nodes
eavesdrop on open HTML
MITM on ADH
protocol failure
SSL failure
implementation
leakage
Insider attack
- client-side
identity loss
theft by insider
shared identity
post-it identity
eavesdropping on machine
keyloggers
remote admin tools
system escrow tools
server-side
sysadmins
db access
data entry
application dependent
theft of user & transaction data
social engineering attack
outsider breaches security
change to password, etc
whos problem?
outside perimeter of SSL
effects risk calculation
calculations only possible by user
not wise to impose costs
install breached software
into source code repository
set up fake download path
direct access to host
the insider advantage
perversion of investigation
knowledge of weaknesses
governance attack
breach internal controls
skimming
collusion insider/outsider
CA-side
|
| |